In this “guide” I will try to explain how an attacker can gain access to your Wireless Network, and suggest ways you can protect yourself.
Firstly, I will not talk here about whether sharing your internet connection with your neighbors, or whoever passes by, is a good idea or not. This would be indeed an interesting topic to discuss, along with a beer, but it is out of the scope of this article.
Secondly, I will only describe the available attacks in a high level so that this article can be understood by as many people as possible. However, in the near future I will also write a lower level/advanced guide for attacking wireless networks, that you can check for more specific details.
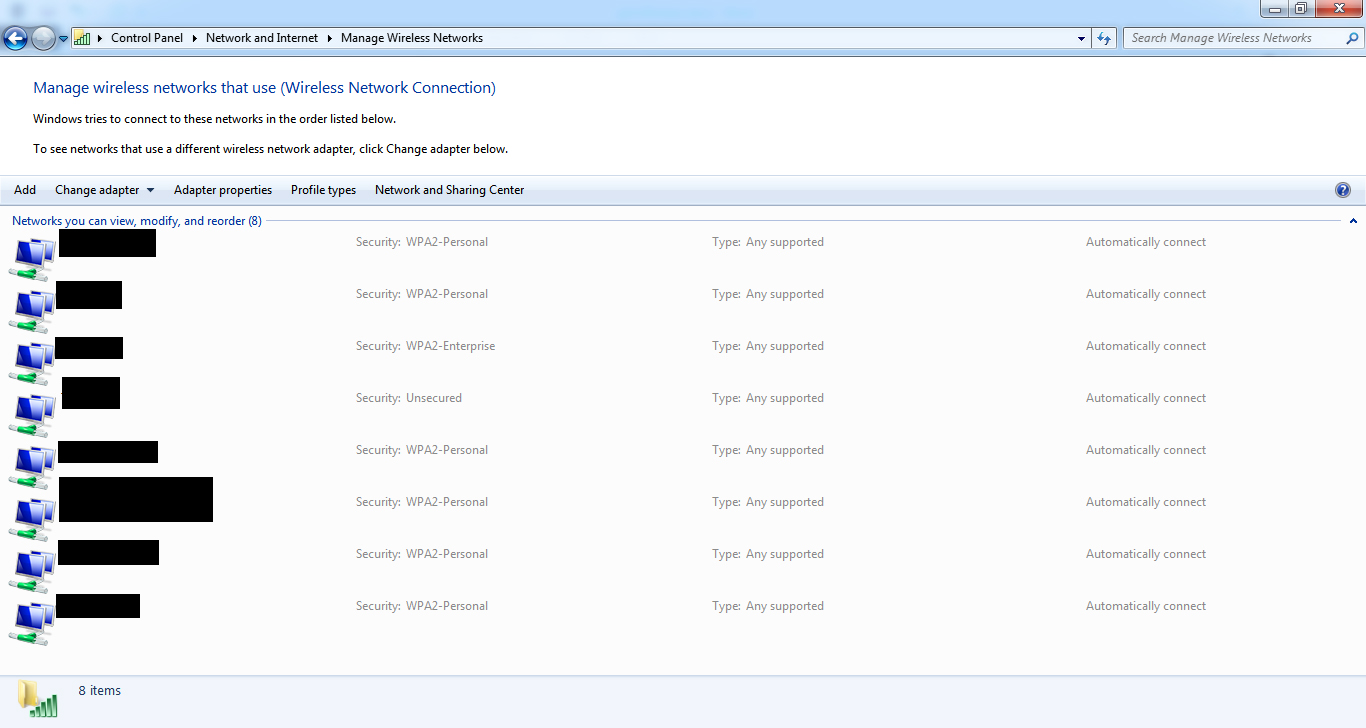
Generic Info 1: You might be wondering, how can I even know what kind of protection I use in my wireless?
In a Windows 7 machine, navigate to Control Panel/Network and Internet/Network and Sharing Center/Manage wireless networks. Here you can see a list with all your wireless networks and their security type.
Generic Info 2: In the following you might start wondering, and how can I login and check my routers settings?
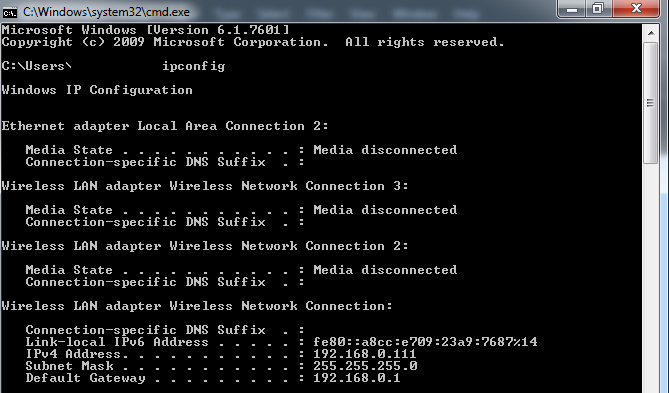
Firstly you need to find your routers IP address. To do this (windows) go to Start/Run and type cmd (or cmd.exe). There type ipconfig and you will get something like:
Now this default gateway (192.168.0.1) is what you are looking for. Open a browser and type 192.168.0.1 (instead of google.com or whatever). There you go! Now probably you have to login. If you never changed your password you have to use the defaults (sometimes admin/admin or admin/password) you can usually find this info on your router itself (in a sticker). Afterwards, you can start checking your settings. I won’t get in much details here since this is router-specific.
So, lets start!
Open (Unsecured) Wireless Networks:

While one would expect that nowadays it is really hard to find wireless networks that are just open, this is not true. In many cases airports, coffee shops, hotels, etc. use open wireless where after you connect you are automatically forwarded to their webpage in which you have to put some credentials that they provided (either for free or as a paid service).
In an open wireless network, everything you do can be easily seen by others. Especially, visiting unencrypted websites (whatever has http instead of https), or even worst logging in such a website simply gives out all your information to potential attackers. The same applies to message clients, e.g., windows messenger. Be aware that in some cases even (encrypted) https sites can be manipulated in such a way that an attacker can get your credentials! In general, in these kind of networks expect no privacy or security at all!
Summary/Suggestions: Do not use open wireless networks! If this is your friends’ network try to explain the risks! If its a hotel/university/etc network and you are somehow “forced” to used, again try to complain about it. If everything fails and you just have to use an open wireless network the usage of a VPN (virtual private network) is the only solution I can think of.
WEP-protection:
WEP (or wired equivalent privacy) is an ancient (1999) security algorithm for wireless networks. Usually, from the attackers’ perspective, WEP-protected networks are becoming rare and hard to find. However, this can also be country-related (due to a so-called digital gap, different security policies by internet providers, etc). For instance, in my experience, it is much easier to find WEP-protected networks in Greece rather than in Germany. Nevertheless, these networks will disappear as the time passes by. This is because I do not think that there are router manufacturers out there that still produce WEP-based (by default) routers or Internet Service Providers (ISPs) that are ok with it.
Due to severe cryptographic/algorithm flaws, WEP can be easily cracked in a couple of minutes. By the way, this is totally unrelated with your password’s strength. It does not matter if your password is 1234567 or a large random one.
Summary/Suggestions: Do not use WEP protected wireless networks! If this is your friends’ network try to explain the risks! WEP networks are the worst because they provide the user a “feeling” that she is secured. However, let me repeat it: WEP can be hacked in a matter of minutes!
WPA/WPA2 (psk) protection: 
WPA2 (Wi-Fi Protected Access II) is currently the state-of-the-art in wireless security. In general, most of the wireless routers you already have (or you buy nowadays) should be able to support this. With some work these networks can be quite hard/almost impossible for an attacker to crack.
Good to know:
The WPA2 supports passwords with a range from 8 to 63(!?!) characters.
SSID is simply your networks name, e.g., antifa-wireless, linksys, eduroam, etc.
Weak Passwords
The most common attack in a WPA network is password-related. Basically, the attack is based on the fact that every time you connect to your network a cryptographic “handshake” takes place between you and your router. Anyone can quite easily eavesdrop and get all the data of this handshake.
Are you already hacked?
-No.
What the attacker has is just an encrypted set of data. In order to successfully crack your network and find your wireless password (WPA key) she has to deploy a dictionary attack. In such an attack, the “stolen” data set will be compared with a list of possible passwords that the attack has. This means that if you are using a really weak password (e.g., 12345678) you are indeed doomed. A huge amount of specialized, for WPA, dictionaries exist online.
What can you do?
Use a random password of at least 13+ characters and with all kind off possible characters (a-z, A-Z, 0-9, !-*). (I will write an article specifically tailored for passwords soon.) In addition, try to change your SSID (networks name), to something personal/random, that of course is not anyhow related with your password! WPA cryptography enhances its security by using your network’s name in the cryptographic process. However, huge password datasets (so-called rainbow tables) exist for well-known/default SSID networks (https://wigle.net/gps/gps/main/ssidstats). This means that if your network is named “genderissociallyconstructed” it is more secure than a default “Linksys”.
Am I secure now?
-Maybe, check the WPS Vulnerability and Router Specific issues.
WPS vulnerability
WPS (Wi-Fi Protected Setup) is not related with the WPA protocol itself. WPS started in order to “allow home users who know little of wireless security and may be intimidated by the available security options to set up Wi-Fi Protected Access, as well as making it easy to add new devices to an existing network without entering long passphrases”.
The scenario is as follows: you have a very strong password that you don’t even remember for your WPA network. Then a friend comes and wants to connect. So, instead of giving her this strange random password, you simply press a button in your router and she is automatically authenticated.
Magic, right? No, due to the crappy implementation of WPS an attacker can now try to find your WPS password (usually automatically generated by your router and only 8 chars long!). So, in practice, depending on your router, an attacker could crack your WPS (and then also get your WPA key) in about 4 to 8 hours!
What can you do?
Try to firstly check if your router has a WPS functionality. Fast way is to check your router for a WPS button or for related info on its sticker like bellow:
Now, if it is WPS enabled, you can try to disable the WPS from your routers settings. However, keep in mind that in some cases even disabling the WPS doesn’t stop an attacker to actually attack your WPS!?! Other ways to protect yourself is to buy a new router or upgrade your routers firmware.
Router Specific issues
Finally, another possible attack could be related with your router itself. This is the case when you left your default WPA password generated by your router. Basically, if you never changed your password this is the case!
So what happens is that in some (not so rare) cases certain routers generate their WPA keys in a non-random way. To find if your router has certain vulnerabilities you can simply google it. This can be country/manufacturer/router specific. For instance, in Germany routers/SSIDs like EASYBOX, Vodafone, WLAN-“number” etc are vulnerable. You can solve this issue by not using the default WPA key of your router.
Summary/Suggestions: WPA2 can be considered secured when you have a strong password and your WPS is disabled.
Others
Social Engineering:
Social Engineering refers to “psychological manipulation of people into performing actions or divulging confidential information”. While it might sound trivial social engineering techniques can really destroy all your security efforts. In our case this could include a neighbor asking for your wireless password (for whatever reason), someone breaking in your place, etc. Am I getting paranoid here? Maybe, just keep in mind these things.
Techniques that do not really work:
-MAC-filtering: Every computer/router/smartphone/etc has a “unique” hardware id called MAC. It is indeed possible from your router settings to create a list (this is called whitelisting) with MACs that you trust (your laptop, etc) so that they will be the only ones that can connect to your network. However, this technique doesn’t work in practice as it is extremely easy to:
1. See connected machines in a wireless network (and their MACs).
2. Impersonate yourself with one of these trusted ids.
3. Connect to the network.
-Turning off SSID broadcasting: You can also disable the broadcasting of your network. This means that someone with a Windows7 machine won’t be able to see your wireless network with a simple check. From a hackers perspective this is for no use since your network will be indeed shown when scanning all the wireless networks (just without an SSID name).
Not covered in this guide
WPA-TKIP vulnerability: Not covered since it cannot be really/practically used.
Hopeypot SSID attacks: I might write something about this in the future.
Paranoid stuff: Well, there are “alternative” ways that you could apply to “protect” your wireless network. For instance, one can try to reduce to signal strength of her router by putting it in the cupboard (or wherever). Other approaches would be the usage of “Wi-Fi blocking paint” in your room (http://news.bbc.co.uk/2/hi/technology/8279549.stm), degrading your router from 802.11n to 802.11g, or even lower to 802.11b, etc. While some of these things are fun, its more like a security by obscurity approach that I do not really suggest.